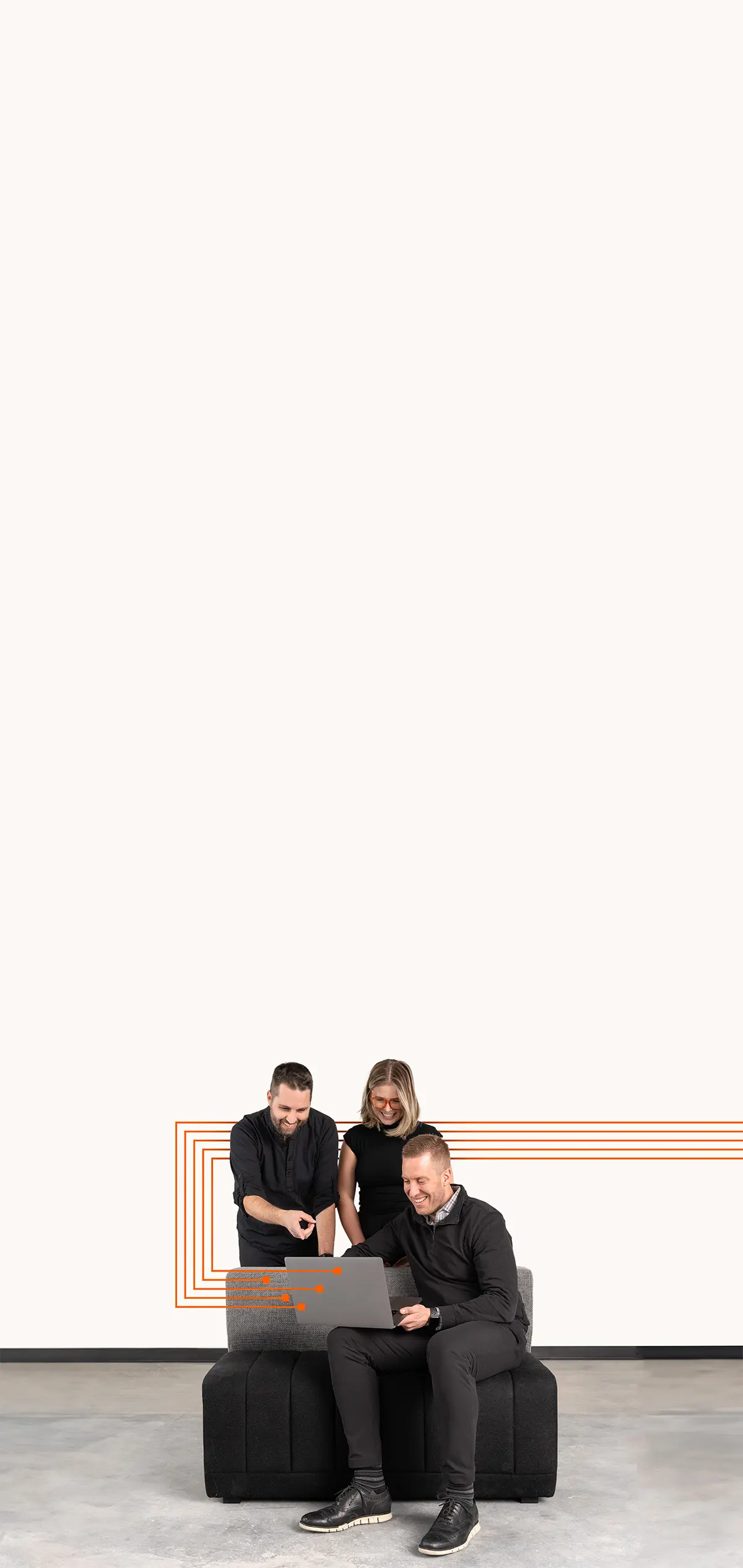
Executive blog
Hear from security leaders at NetSPI as they explore the latest cybersecurity strategies and the most impactful trends affecting the industry today.
Our favorite picks

A New Era of Proactive Security Begins: The Evolution of NetSPI
Introducing The NetSPI Platform, the proactive security solution used to discover, prioritize, and remediate the most important security vulnerabilities. Plus, get a first look at NetSPI’s updated brand!

Ask These 5 AI Cybersecurity Questions for a More Secure Approach to Adversarial Machine Learning
These questions will kickstart your journey into Adversarial Machine Learning and AI security with key considerations from the start.

Annual Pentest? Done. How Proactive Security Covers the Other 50 Weeks in a Year
Explore proactive security from a CISO’s lens. Tim MalcomVetter and Aaron Shilts discuss shifting from point-in-time pentesting to proactive security.

The Strategic Value of Platformization for Proactive Security
Read about NetSPI’s latest Platform milestone, enabling continuous threat exposure management (CTEM) with consolidated proactive security solutions.
The Rapid Evolution of AI Voice Cloning and its Implications for Cybersecurity
Learn about the rise of AI voice cloning, its cybersecurity challenges, and necessary measures for IT and InfoSec leaders to stay protected.

5 Essential Cybersecurity Leadership Tips for Technologists
Learn about Sam Horvath’s journey from pentester to Managing Director at NetSPI, with cybersecurity leadership tips for aspiring technologists.
The Balancing Act of In-House vs Third-Party Penetration Testing
Discover how combining in-house and third-party penetration testing brings a hybrid approach to enhance your cybersecurity strategy.
4 Key Themes from Black Hat USA 2024
See NetSPI’s key takeaways from Black Hat USA 2024, including AI hype, pentesting automation, and the importance of third-party risk management.

Improving Ransomware Detection with Breach and Attack Simulation (BAS)
Explore how breach and attack Simulation (BAS) can enhance your ability to identify and mitigate ransomware threats early in the cyber kill chain.
How to Navigate the Stiff-Arm When Protecting Your Generative AI Initiatives
Learn to effectively protect generative AI initiatives by integrating proactive security measures and gaining business buy-in for safer deployment.

CrowdStrike Global IT Outage: Time to Reflect on the Process for Security Vendor Updates?
The CrowdStrike-Microsoft global IT outage sparks reflection of the push and pull of velocity, hygiene, and change management in cybersecurity.

How Threat Actors Attack AI – and How to Stop Them
Learn about common AI attack paths that threat actors use and how you can bolster your own AI security with AI/ML penetration testing.

17 Resources You Can’t Miss When Starting Your Career in Application Security
Entering a career in application security? This guide highlights reputable resources to help aspiring defensive AppSec engineers improve their skills.

Impact Analysis: regreSSHion OpenSSH Vulnerability (CVE-2024-6387)
Read The NetSPI Agent’s take on the impact and exploitability of the regreSSHion OpenSSH vulnerability that could lead to unauthenticated RCE.

Mission for Mainframe | Part 1: Relevant Today
Learn from Michelle Eggers why mainframes are so important as the backbone that keeps our financial systems and other critical industries running.

